The latest version of Apple’s software has a glaring hole in it: You can log in with just the username "root."
It turns out you don't need a password to log in to a locked Apple device using MacOS High Sierra -- just the username "root."
By heading to your device's System Preferences, under Users & Groups, you can click on the lock and get hit with a prompt asking for a username and password to change settings. Then, instead of entering a password, you can type in "root" for the username and leave the password field empty.
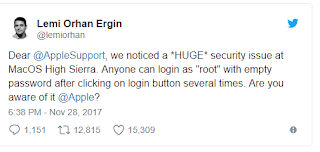
After clicking unlock several times, it should eventually open up, no passwords necessary. Lemi Orhan Ergin, the founder of Software Craftsmanship Turkey, discovered the security flaw and tweeted it out to Apple Support on Tuesday.
"We are working on a software update to address this issue," an Apple spokesperson said. "In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here. If a Root User is already enabled, to ensure a blank password is not set, please follow the instructions from the 'Change the root password' section."
The simple exploit means anybody with physical access to your MacOS High Sierra device can log in on your computer, no matter how secure your passwords are.
Amit Serper, a security researcher from Cybereason, demonstrated that the bug works even on the login screen after restarting the computer:
The bug works for every aspect of the OS that would normally require a password, which means someone could also get access to your Keychain, containing all your passwords.
MacOS High Sierra was also plagued with a password issue when it launched, after a former NSA hacker showed that he could extract sensitive data from Keychain using an app downloaded online.
There's a workaround for the "root" flaw until Apple fixes it. You can turn guest users off, or change the root password from your directory utility, as 9to5Mac suggested.
How to secure your device?
Apple has already rolled out an update for it. But for the time being, if you haven't got the update you can do this simple trick to fix it. Create a username "root" and set a password to it.
Source: CNET
It turns out you don't need a password to log in to a locked Apple device using MacOS High Sierra -- just the username "root."
By heading to your device's System Preferences, under Users & Groups, you can click on the lock and get hit with a prompt asking for a username and password to change settings. Then, instead of entering a password, you can type in "root" for the username and leave the password field empty.
 |
| Demonstration |
After clicking unlock several times, it should eventually open up, no passwords necessary. Lemi Orhan Ergin, the founder of Software Craftsmanship Turkey, discovered the security flaw and tweeted it out to Apple Support on Tuesday.
"We are working on a software update to address this issue," an Apple spokesperson said. "In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here. If a Root User is already enabled, to ensure a blank password is not set, please follow the instructions from the 'Change the root password' section."
The simple exploit means anybody with physical access to your MacOS High Sierra device can log in on your computer, no matter how secure your passwords are.
Amit Serper, a security researcher from Cybereason, demonstrated that the bug works even on the login screen after restarting the computer:
The bug works for every aspect of the OS that would normally require a password, which means someone could also get access to your Keychain, containing all your passwords.
MacOS High Sierra was also plagued with a password issue when it launched, after a former NSA hacker showed that he could extract sensitive data from Keychain using an app downloaded online.
There's a workaround for the "root" flaw until Apple fixes it. You can turn guest users off, or change the root password from your directory utility, as 9to5Mac suggested.
How to secure your device?
Apple has already rolled out an update for it. But for the time being, if you haven't got the update you can do this simple trick to fix it. Create a username "root" and set a password to it.
Source: CNET

Comments
Post a Comment